These invisible images let companies spy on your email — here’s how to stop them
Block people from spying on you with email trackers

Your emails are spying on you. Out of the gazillion emails that hit our inboxes every day, most of them have hidden trackers capable of informing the recipient when you open them, where you open them, how many times you’ve read them, and much more — a privacy nightmare many call “endemic.” Fortunately, there are ways you can protect yourself and your inbox.
Advertisers and marketing companies, especially, equip their promotional emails with tracking pixels to keep tabs on their mass campaigns. Based on how people interact with them, senders can learn which subject lines are the most “clickable,” and which of their targets can be potential customers.
Though this is useful from an analytics perspective, it’s also often done covertly and without consent. Not a fan of this invasion of privacy? There’s an easy way to turn off email tracking. , For a better look at what these intrusive little pixels are and how to put an end to them, read on.
What are email tracking pixels?
The email tracking pixel is a surprisingly simple concept that allows anyone to secretly gather loads of information on you as soon as you interact with their messages.
When someone wants to track whether you’ve read their email, they embed a tiny 1 pixel by 1 pixel image inside it. Once you open the email, it pings the server where the image is stored and logs the interaction. Not only does the sender trace whether you have clicked their email and how many times it's been clicked on, it can also tell your location by checking where that network ping was launched and which sort of device was used.

There are two reasons why you never actually see that tracking graphic. One, it’s minuscule. Two, it’s in the GIF or PNG format, which allows the company to keep it transparent and invisible to the naked eye. Oftentimes, a sender will also hide this in their signature. Therefore, that fancy font or the flashing company logo you find at the bottom of a commercial email might be more than a harmless, cosmetic presence.
More importantly, studies have found that it’s possible for advertisers and other malicious actors to link your email activities with your browser cookies by matching your location and device specifications. This opens an alarming can of worms since it enables them to identify you wherever you go online, connect your email address to your browser history, and much more.
“The results belie the claim of 'anonymous' web tracking," one study warned.
Stay in the know with Laptop Mag
Get our in-depth reviews, helpful tips, great deals, and the biggest news stories delivered to your inbox.
Find out which emails are spying on you
If email tracking pixels are invisible, how do you spot them? Most email clients like Gmail and Outlook don’t have a built-in mechanism for this, but you can turn to third-party tools.
For Gmail, we suggest a Chrome and Firefox extension called Ugly Email. It adds a little “eyeball” icon next to the emails that are loaded with tracking pixels and then blocks them from spying on you. Alternatively, if you’re a Yahoo or Outlook user, you can try Trocker, which similarly marks emails with trackers on their websites.
These extensions, though, are limited to your computers. To detect email trackers on your phone, you’ll need to subscribe to a premium email client like HEY.
How to block email tracking pixels
Tune your existing inbox
Since email trackers rely on hidden media attachments, they’re fairly straightforward to block. The easiest method is to simply prevent your email apps from loading any images by default and only do it manually for the emails you trust or when there’s an attachment you’d like to download.
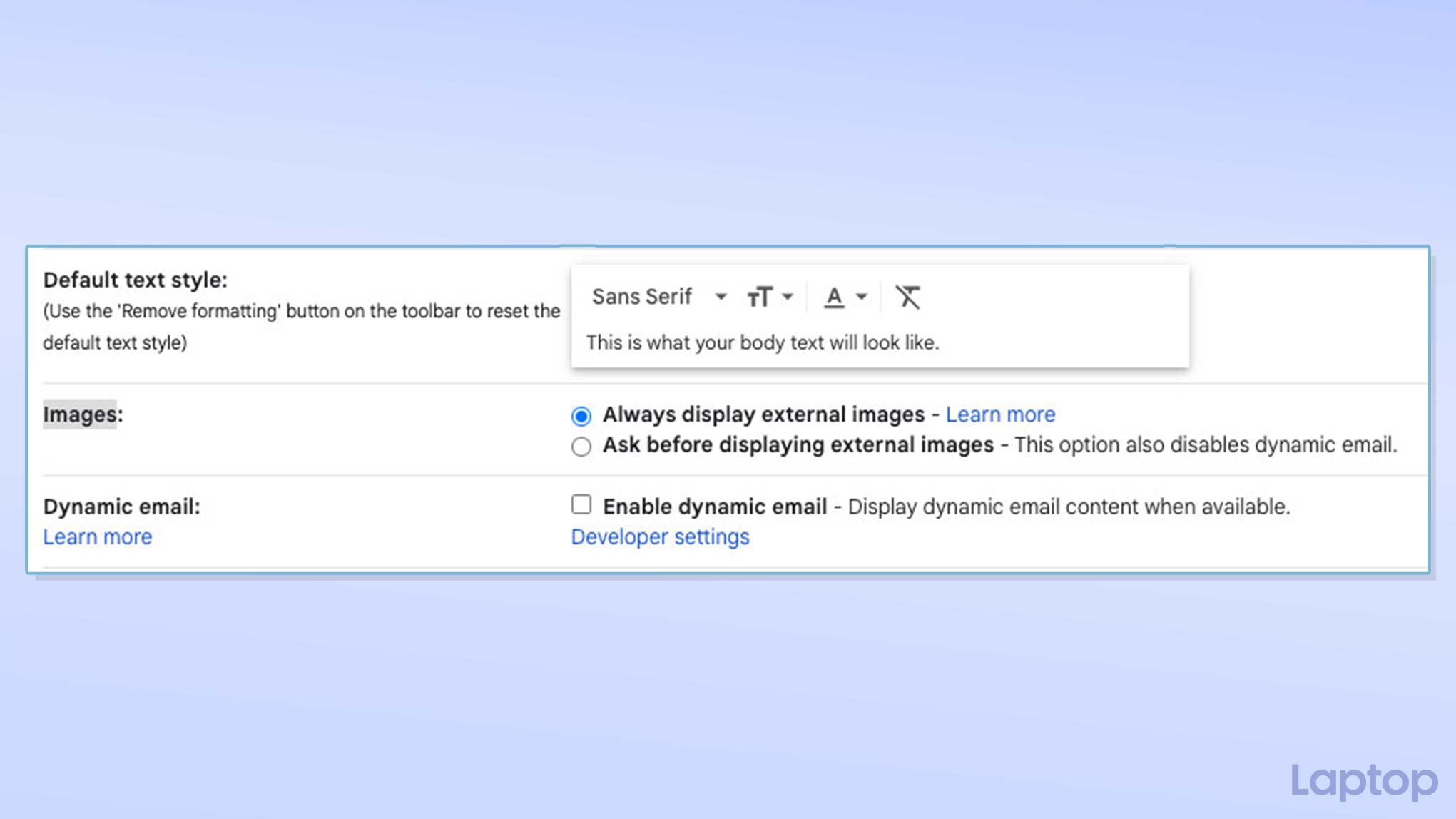
On Gmail, the option to block external images is available under Settings > Images > Ask Before Displaying External Images on the web and mobile apps. On Outlook apps, it’s found under Options > Block External Images on mobile and Options > Trust Center > Automatic Download on desktop.
Though Apple Mail also lets you accomplish this from Preferences > Viewing > Load remote content in messages, you can directly block trackers on it as long as you’re on macOS Monterey. Head over to Mail > Preferences > Privacy and check the “Protect Mail Activity” box.
Get a private relay email address
The problem with the methods we’ve discussed so far is that they block the tracking pixels after the email has already landed in your inbox — they don’t strip the email of them. For ensuring you never accidentally open an email with trackers, you’ll need a proxy address that pats down your messages and removes any contraband before they arrive in your inbox. Another benefit of this is that it allows you to keep your personal email address private and only hand out a relay ID to websites, newsletters, and others.
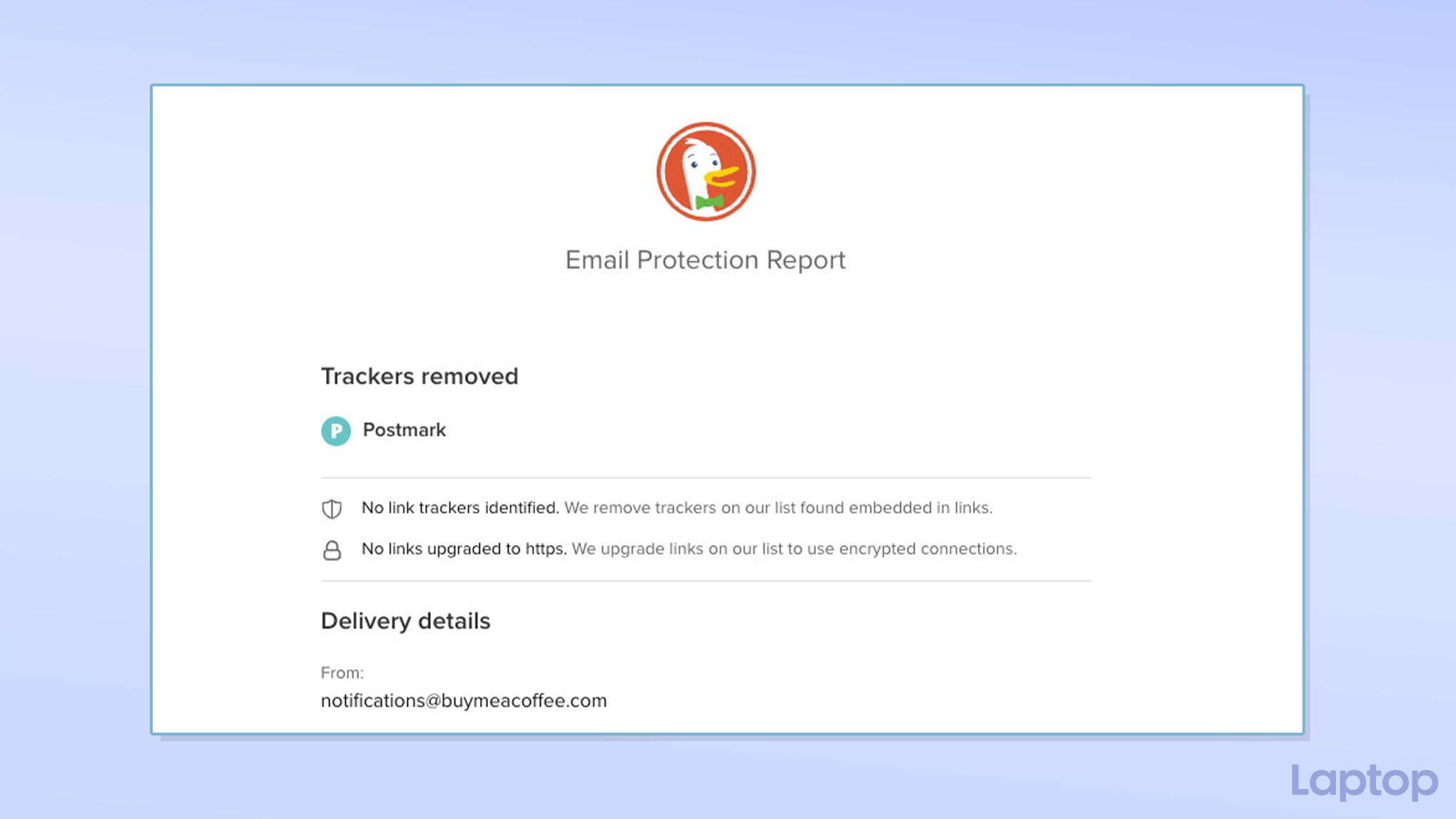
There are plenty of free services that offer a proxy email address. We recommend DuckDuckGo’s Email Protection. It lets you create a new custom relay address, which, before forwarding your mail to your personal inbox, secures them by booting the trackers and encrypting any unsecured links in the body.
At the top of forwarded emails, DuckDuckGo also adds a little section that tells you whether it found any trackers in it and if it did, which companies were responsible for it.
On an Android phone or iPhone, go to Settings > Email Protection on the DuckDuckGo app to sign up. On a desktop, you can get started with the DuckDuckGo browser extension or its browser for Mac.
Shubham Agarwal is a freelance technology journalist from Ahmedabad, India. His work has previously appeared in Business Insider, Fast Company, HuffPost, and more. You can reach out to him on Twitter.
