Here’s why the Google Play Store is a malware infected hellscape
Sneaky scoundrels subvert security steps

Not a week goes by without the Google Play Store playing some part in delivering a strange new malware designed to steal from or spy on Android users — if it’s a good week, it’ll even manage both.
Many have been left puzzled by how the Google Play Store became more riddled with viruses than a sailor on shore leave — but not Google, who seem to have figured out how hackers are manipulating its platform to their benefit.
Google Play Store: A weakness exposed
A recent threat report published by Google’s Cybersecurity Action Team indicated that, in spite of a recent spike in cases, less than 1% of all downloads from Google Play are what the company calls Potentially Harmful Applications (or PHAs).
Google thoroughly evaluates all apps before release onto the Google Play Store and when PHAs are detected they’re quick to act — promptly removing apps and terminating developer accounts.
However, knowing this to be the case, dastardly developers have switched tactics. Instead of allowing a harmful app to go through Google’s evaluation process and risk getting flagged as a PHA, malicious actors will submit an innocuous and seemingly legitimate app for Play Store evaluation at first to gain Google’s trust.
However, once the app is on the Play Store it will receive an update from a third-party server — altering the app's code and functionality, allowing malicious extensions to execute freely.
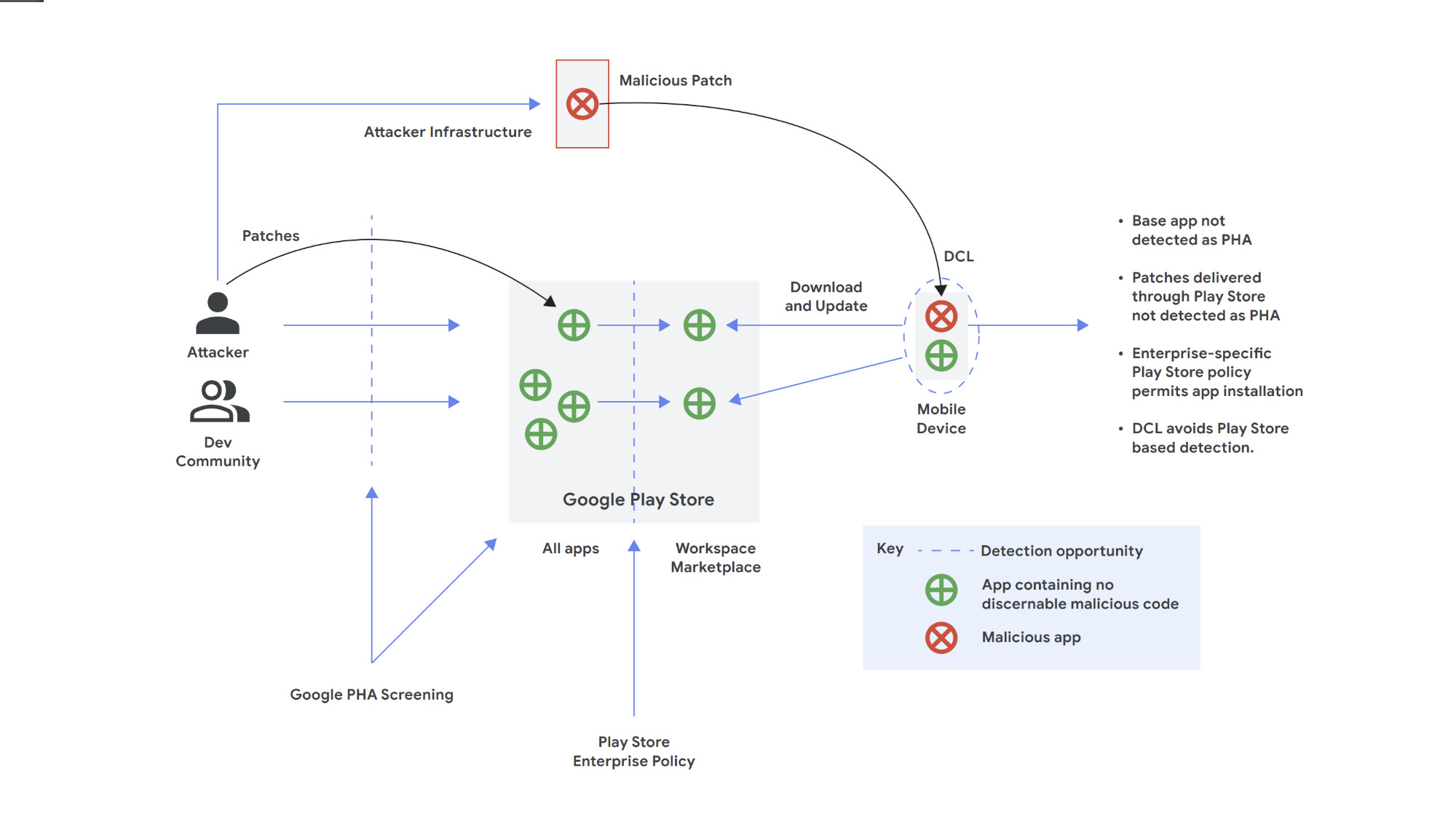
Versioning: How good apps go bad
This process is called versioning — a circumvention of Google Play’s policy against any apps that can “modify, replace, or update itself using any other method than Google Play’s update mechanism.”
Stay in the know with Laptop Mag
Get our in-depth reviews, helpful tips, great deals, and the biggest news stories delivered to your inbox.
Google has identified one instance of versioning as Dynamic Code Loading (or DCL). DCL apps have the potential to download and run code from untrusted sources beyond the walled garden of the Google Play environment. This allows previously legitimate apps to bypass Google’s PHA checks and convert themselves into malware or spyware right under Google’s noses.
Google does state that apps making use of DCL “violate Google Play Deceptive Behavior policy and may be categorized as a backdoor.”
Outlook
While Google has identified one of the main pipelines to malicious apps appearing on its platform, the report fails to indicate exactly how they plan to combat it. However, it’s highly unlikely that the Cybersecurity Action Team behind the report are willing to allow malicious actors to continue with their efforts for much longer.
Could we see a Play Store crackdown on DCL apps in the near future? Quite possibly. Google will no doubt be keen to patch up its app platform's biggest security flaw and hard at work on sealing shut any backdoor vulnerabilities currently being exploited.
For news, rumors, and updates on all things cybersecurity and tech, follow Laptop Mag on Twitter, Facebook, and Flipboard for the latest word as it arrives.

Rael Hornby, potentially influenced by far too many LucasArts titles at an early age, once thought he’d grow up to be a mighty pirate. However, after several interventions with close friends and family members, you’re now much more likely to see his name attached to the bylines of tech articles. While not maintaining a double life as an aspiring writer by day and indie game dev by night, you’ll find him sat in a corner somewhere muttering to himself about microtransactions or hunting down promising indie games on Twitter.
