Windows 10 update accidentally broke Google Chrome’s security
How a single line of Windows 10 code broke Google Chrome’s security

In a meeting of security fail regulars, a Windows 10 kernel bug was found to be creating a serious vulnerability in Google's Chrome web browser.
The problem was uncovered by the Project Zero team at Google. Introduced as part of the Windows 10 1903 update on May 21 of last year, the mistake reveals the catastrophic effects a single line of code can have (via BleepingComputer).
- How to Upgrade to Windows 10 for free in 2020
- Best laptops 2020
- Windows 10 May 2020 update: What's new and how to download it
The vulnerability in question, identified as CVE-2020-0981, was fixed as part of an April 2020 update to Windows 10, but it's an instructive look at how easily security measures can break down as a result of even minor changes across the myriad lines of code in Windows 10.
Here's the original line of code:
NewToken->ParentTokenId = OldToken->TokenId;
And the Windows 10 1903 update to the code:
NewToken->ParentTokenId = OldToken->ParentTokenId;
Sign up to receive The Snapshot, a free special dispatch from Laptop Mag, in your inbox.
The change in question created a token security feature bypass that Chromium was dependant on to maintain its secure sandbox. Rather than limiting new sandboxed processes to Restricted Tokens, it allowed a new sandboxed process to have a token that could be "considered a sibling of any other token on the desktop."
This fundamental break in a core Windows 10 security feature that the Chromium team was building off of, allowed Project Zero security researcher, James Forshaw, to create a complicated chain of events that exploited multiple Windows 10 vulnerabilities and would have allowed an attacker to escape the secure Chromium sandbox.
This is the diagram of Mr. Forshaw's exploit, just to give you an idea of the complexity.
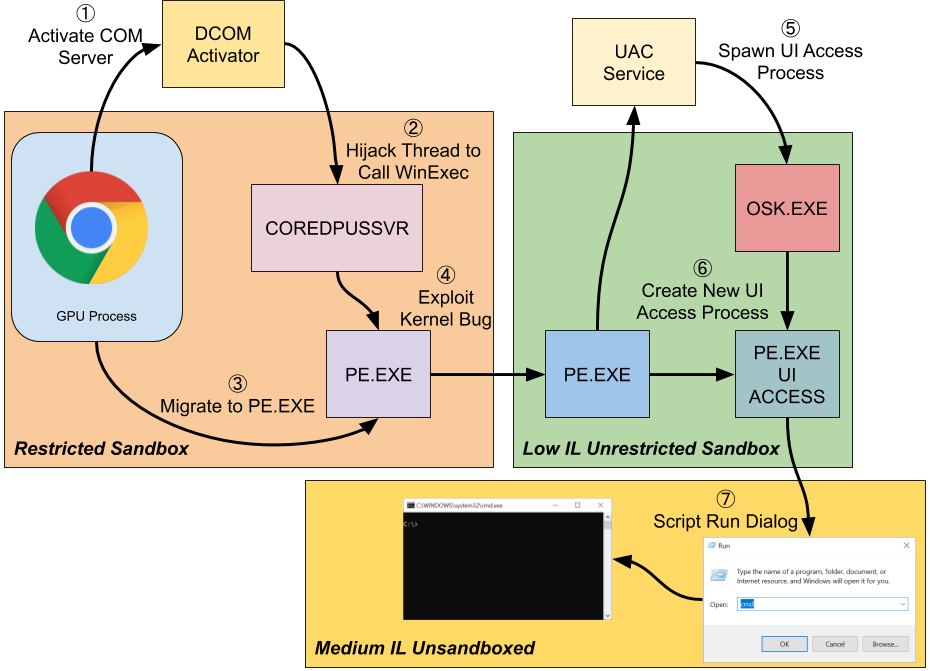
If you want to read the technical breakdown of the flaw along with Mr. Forshaw's full description of his sandbox escape method, you can read his account on the Google Project Zero blog.
Sean Riley has been covering tech professionally for over a decade now. Most of that time was as a freelancer covering varied topics including phones, wearables, tablets, smart home devices, laptops, AR, VR, mobile payments, fintech, and more. Sean is the resident mobile expert at Laptop Mag, specializing in phones and wearables, you'll find plenty of news, reviews, how-to, and opinion pieces on these subjects from him here. But Laptop Mag has also proven a perfect fit for that broad range of interests with reviews and news on the latest laptops, VR games, and computer accessories along with coverage on everything from NFTs to cybersecurity and more.

