How to do 2FA right: Getting started with two-factor authentication
Here’s how to do 2FA right from the start

Two-factor authentication (2FA) used to seem like something reserved for spy movies or political thrillers — the sort of thing Mission Impossible’s Ethan Hunt needs to use to access his assignment before it self-destructs. But that’s not the case anymore. Virtually all of us are using 2FA on a daily basis, whether that’s biometric 2FA on our devices (fingerprint or facial recognition) or the common one-time passwords that are obtained via SMS or an authenticator app.
Our accounts are just too valuable for hackers to ignore. Even a compromised email account can be a stepping stone to gaining access to financial accounts and robbing you of your hard-earned money while creating a nightmare scenario for you. Although movies depict a hoodie-clad hacker with fingers flying furiously over the keyboard, the reality is that according to the 2021 Verizon Data Breach Investigations Report the overwhelming majority of security breaches (85%) involve a human element. 2FA is the best way to combat this kind of attack.
- Best VPN services 2021
- Norton Antivirus app now lets you earn crypto — here's what you can mine
- The best laptop deals in June 2021
Whether you think this is a real concern for you or not, many companies are moving to 2FA as a required security measure with Google being one of the most recent to announce it will require 2FA in the near future.
We recently covered why you need to stop using your phone number for two-factor authentication, if you missed that and aren’t sure why that’s such a bad idea give it a read and come back, now we’re going to show you how to do 2FA the right way.
What is two-factor authentication?
2FA is the most well-known and widely used form of multi-factor authentication (MFA), which as the name suggests relies on multiple factors in order to verify your identity. A classic example is getting money from an ATM, you need the card as well as your PIN in order to access your account.
That example includes two of the three categories for MFA, “what you have” (a physical object) and “what you know” (a password or security question). The third option is “what you are” meaning a biometric method like a fingerprint scanner or facial recognition. Unlike even an incredibly complex password, this eliminates the possibility of a breach of your account without physical access to you.
In Google’s aforementioned 2FA announcement, it referred to passwords as “the single biggest threat to your online security.” For now, passwords are still very much a part of the 2FA process for most people. However, the point stands that they are the weak point in the chain that needs to be bolstered by at least one additional factor. So let’s take a look at the best options for 2FA.
Stay in the know with Laptop Mag
Get our in-depth reviews, helpful tips, great deals, and the biggest news stories delivered to your inbox.

App-based two-factor authentication
As with just about everything, there are app solutions to deal with 2FA, these are called authenticator apps. There are dozens on the market, but a few that I would recommend are Authy, Microsoft Authenticator, LastPass and 1Password. Google Authenticator is another popular option, but I dislike that it doesn’t require either password or biometric login, it’s a potential security gap in a process that is trying to eliminate them.
Authy is a dedicated authenticator app and is expressly used for 2FA login. Microsoft Authenticator, LastPass, and 1Password are password managers that have incorporated an authenticator component. If you need a password manager or already use one of these, I would go this route as it makes the 2FA process as frictionless as possible.
Once you choose your authenticator app and have it installed, you can begin setting up 2FA for your accounts. This is going to be the most tedious part of the process as it involves visiting any service or site that you use that offers 2FA support one by one. I suspect this is the step that puts most people off using 2FA, but it’s ultimately worth it for your online security. And once you have 2FA up and running, it isn’t the hassle that some make it out to be.
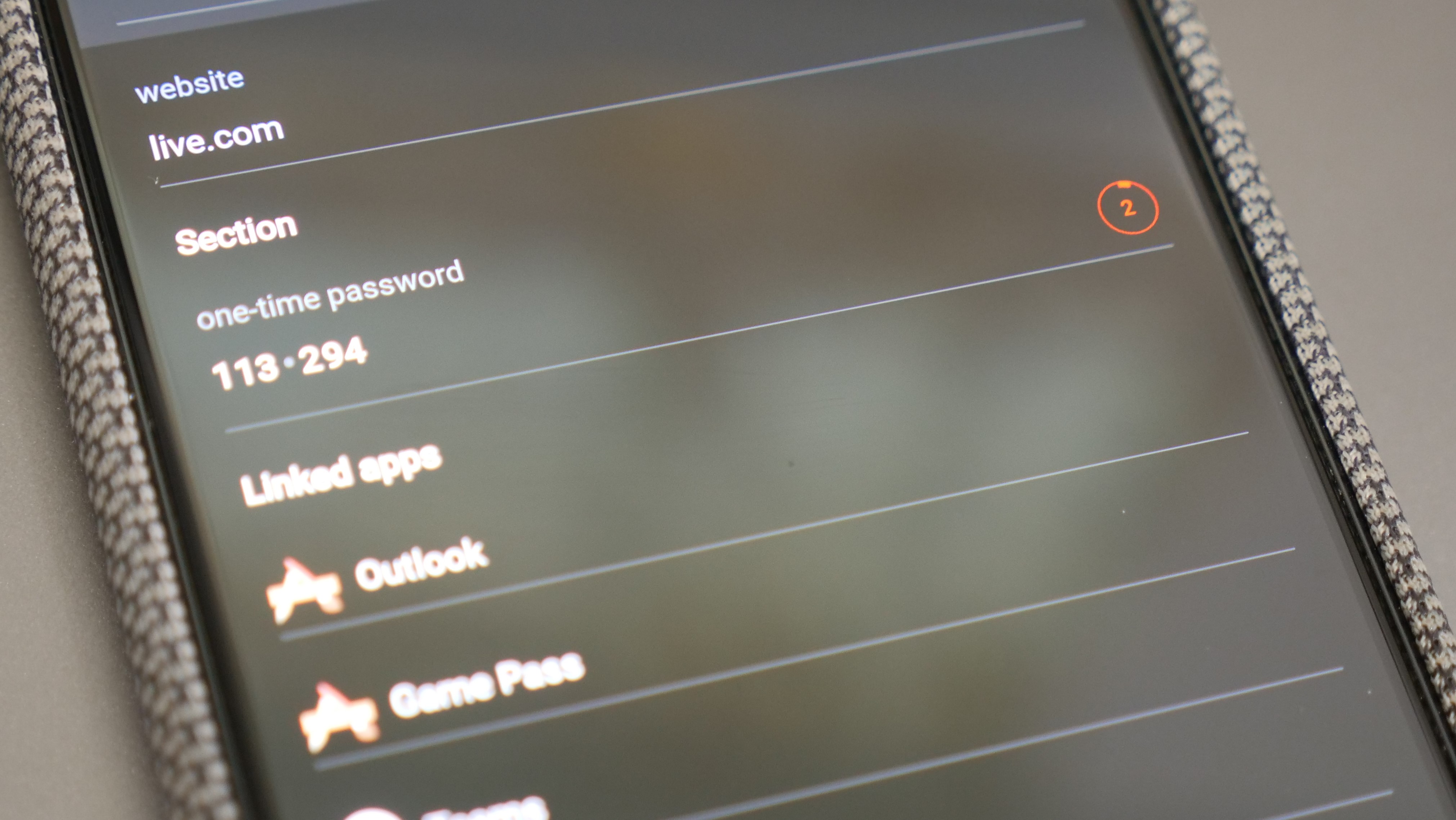
During the initial setup, you will either scan a QR code, or in some cases, enter a code and then that service will be saved in your authenticator app. You’ll see your accounts listed with a set of six digits next to them and a timer counting down. Every 30 seconds a new random six-digit code is produced for each one. These are time-based, one-time passwords (TOTP), similar to what you would get via SMS or email, but these do not require an internet connection and critically can’t be intercepted by anyone.
Now in most cases, you won’t need to enter your TOTP code every time you log in unless you want that level of security. Typically it is only required that you use it when you are logging in on a new device or after a set amount of time has elapsed, 30 days is common, but sites and services will vary on this.

Hardware-based two-factor authentication
Now while there is definitely a convenience factor with mobile authenticators. In a two-year case study with Google, a hardware-based solution was four times faster, less prone to requiring support and more secure. A hardware MFA/2FA solution looks a lot like a USB flash drive. They come in different shapes and sizes offering support for any of your devices with USB Type-A, USB Type-C and Lightning. Some modern options will also offer wireless support through NFC or Bluetooth.
With these security keys, you simply plug them into your device or swipe them over the NFC chip on your device and that serves as your 2FA method. This is the “what you have” MFA category. It’s easy to see how that is going to be faster than having to open your authenticator app, find the relevant TOTP code and then enter it before it resets.
Just like the authenticator apps, there are a considerable number of options when it comes to 2FA hardware. The most prominent (and the one Google went with for its over 50,000 employees) is YubiKey. Google itself has its Titan Security Key and Thetis is another strong player in the market, but all of these options are FIDO U2F Certified, an open standard created by Google and Yubico (the company behind YubiKey) back in 2007 to promote broad adoption of secure authentication.
The basic setup process is essentially identical to the mobile authenticator method, you will need to go to each service and follow instructions for setting up 2FA. Rather than scanning a QR code and getting the TOTP codes, you will either plugin or swipe your security key when prompted and it will then be registered with that service. When prompted in the future, you will just have to once again plugin or swipe your security key and tap the contact on it. If you aren’t sure what services and applications you use that support a security key you can refer to this handy catalog from Yubico.

The most common concern with the security key is what to do if you lose it or it breaks. There are a couple of options there. The one that Google employs and Yubico recommends is to maintain two security keys, one that is stored securely and another that you keep on you. With the exception of some of the tiny security keys that are meant to be kept permanently plugged into devices that are in a secure location, all of the security keys have a hole to allow them to be attached to your key ring.
This does mean that anytime you register for 2FA on a new service that you need to run both security keys as it is registering to the physical hardware and not an account, but again after the initial setup, this shouldn’t be that frequent of an issue. These aren’t terribly expensive with the YubiKey 5 NFC for example going for $45 and the Thetis FIDO2 BLE Security Key available for under $30 and you shouldn’t have to replace them for years, so it’s not a bad solution.
The alternative is that you need to keep the backup codes that are provided by all of the sites and services that you use 2FA on. These can either be printed out and stored in a secure location or you could encrypt and store the text files somewhere safe either in a password-locked and encrypted folder or on a flash drive that is securely stored.

Overview
Regardless of whether you opt for an app-based or hardware-based 2FA solution, there’s no question that the initial setup is one of the biggest hurdles given the sheer volume of sites, services and apps that many of us use. I found it easier to just do 3-5 a day until I made my way through all of them rather than going for a single marathon registration session.
Once you are done with that initial process though, it is a pretty painless extra step that offers you so much more security than a password alone or an SMS or email-based 2FA solution. You may chafe a bit at the extra time spent occasionally having to either enter your code or plugin your security key, but it pales in comparison to the headache of having to deal with someone stealing your credentials and potentially turning your life upside down as you try to regain control of your accounts.
With companies like PayPal, Google and others moving to 2FA as a requirement, you are going to need a 2FA solution. Don’t settle for SMS or email-based solutions, they are simply too easily circumvented. Both authenticator apps and hardware security keys offer actual strong 2FA security and following that initial setup process, it quickly becomes a seamless part of your online security habits.
Sean Riley has been covering tech professionally for over a decade now. Most of that time was as a freelancer covering varied topics including phones, wearables, tablets, smart home devices, laptops, AR, VR, mobile payments, fintech, and more. Sean is the resident mobile expert at Laptop Mag, specializing in phones and wearables, you'll find plenty of news, reviews, how-to, and opinion pieces on these subjects from him here. But Laptop Mag has also proven a perfect fit for that broad range of interests with reviews and news on the latest laptops, VR games, and computer accessories along with coverage on everything from NFTs to cybersecurity and more.

